To create a login page to obtain any kind of password, go to shadowave.com and create your account. You will be given an ID, and once you log in, you will find two links starting with the name scamas.
Copy any of the links and send it to the person you want to steal the login details from. If everything goes well, you will see the password of the victim in the “My Victims” folder.
The best way to send the phishing link to your victim is by email, Have a look at this phishing email intended to hack Facebook account.
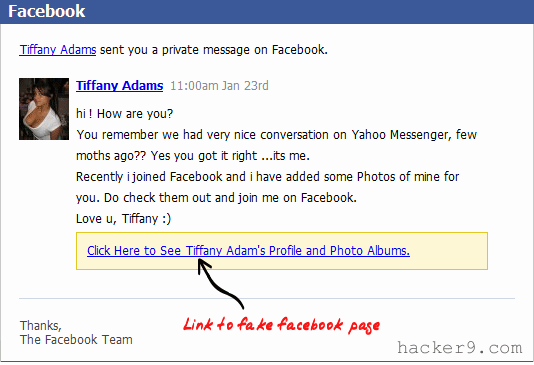
As you can see above, The hacker just tricked his victim in such a way that the fake email from Facebook appears to be the legitimate one.
The disadvantage of this method is, it’s a little difficult to trick people because everyone is aware of it.
This method can be the ideal one, when it comes to hacking users who often browse their Facebook feed on their smartphones as on the smaller screens hardly anyone would check the URL of the web page, isn’t it?.
How to protect yourself
Use the antivirus software with an “anti-phishing” property to protect yourself. Avast is one of such antiviruses with such a great feature. Avoid replying to suspicious-emails or clicking attachments from people you don’t know.
Wherever pop-up-screens appear on your browser, do not put your login information there. You can also tell of any suspicious emails at spam@uce.gov for extra security
Method 2: DNS Spoofing / DNS Cache Poisoning
This is recognized as one of the most dangerous kinds of attacks you can ever perform on your target users. It is hard to detect and works on victims on the same network with the hacker, possibly you.
The trickiest part about this method is that the hacker redirects all-the-requests performed by the DNS server and also all-the-traffic to his or her computer.
Such requests are then manipulated maliciously by the attacker with the main intention of stealing sensitive data.
To use this method in your Facebook hacking endeavour, ensure that you are using Kali Linux OS. It doesn’t matter whether you have dual booted it with windows, or whether it is native boot or VM. Everything will work perfectly.
In addition, see to it that your victim is on the same network with you, either on WLAN or LAN.
Now open the application tab on your computer, go to the Exploitation tools and select Social-engineering toolkit (SET).
Configuring this attack method is easy.
Just open the file etter.conf in the /etc/ettercap/ folder using G-edit program.
Edit the values of gid and uid to 0.
Then go to the line with the name Linux, where it begins by saying whether to use ‘iptables’. Remove the hash sign (#) and you are then done configuring your file for DNS-Spoofing attacks.
Next step is to launch the Ettercap application. You can open it via Terminal by entering “ettercap –G” without quotes.
After opening it, move your cursor to Sniff >> start unified sniffing. Click OK.
Ensure that you choose the correct sniffing-interface you are using on the network. Then navigate to Hosts >> Scan for hosts.
This should take some seconds or minutes to finish according to the speed of your computer or the size of the network. Next is going back to Hosts >> Host list. Here, select your target and choose the DNS spoof to run.
Select the Mitm >> ARP-poisoning and select “Sniff remote connections”. Click OK. Computers on the same network will be sniffed.
You can use “ettercap –T –q –i eth0 –P dns_spoof –M arp // //” command without quotes on your terminal while remote connections are being sniffed. When the target opens any page on Facebook, all their request and traffic will be directed to your phishing-page.
To protect yourself, ensure the websites you are using have an “https” prefix or there is a padlock at the beginning of every URL. Your antivirus is also supposed to be up-to-date for full protection.
Method 3: Using Spy App (Keylogger)
Keylogger is a piece of software that captures the keyboard strokes entered by your victim. Employers use them to monitor their employees.
The fact that it can capture keyboard strokes, it can also capture or record usernames and passwords entered by a person. This is the reason Keyloggers are mostly used as a hacking tool rather than using it as a monitoring tool.
Keylogging is the simplest and the most practical way of hacking Facebook account. Anyone with basic knowledge of software/app installation can install and use it with ease.
These days, spy apps for cellphones are more popular than those designed for computers. This is probably because about 8.9 billion people, according to GSMA-data, are connected to mobile networks globally. That means that almost every adult has a cellphone that he or she uses to surf the internet or use social media networks like Twitter and Facebook.
One of the best spy applications for cellphones is mSpy. To use this application, an attacker must install it in the target user’s smartphone. What it does is, it monitors every keystroke event the user types through his or her keyboard including sensitive data like passwords.
It works in real-time and runs in the background automatically. It is therefore hard for the victim to detect it easily. Once the data is captured, it is sent to the Facebook hacker directly.
I recommend the mSpy app for hacking Facebook passwords and for other sophisticated Spy features that it offers.
Get it here: mSpy – ultimate spy app!
This spy app runs in a complete stealth mode and thus remains undetected.

The app can be used by both business owners and parents. The latter can use it to monitor the online behaviour of their children, and the former to track the activities of their workers.
It works for all the platforms, that is iOS and Android and rooting is not necessarily required. Other than keylogging and checking Facebook messages on Messager, an attacker can use it to monitor or track Call Logs, WhatsApp, and SMS of their target.
Moreover, it can be used to take screenshots, view photos, contacts, and among others remotely. The app is worth using and is currently in the 6th version.
Once you become a member of mSpy, your task is to install the spy app module on your victim’s smartphone.
It’s comparatively easy to install this app on your kid’s or spouse’s smartphone then your friends or any other smartphone that you don’t have physical access to.
Targeting a remote smartphone is a bit difficult job. However, It is not impossible as our brains come pretty much hard-wired to be tricked
Professional hackers do this by using various social engineering techniques, for example, if I were gonna install this spy app on my friend’s smartphone, I would wait and watch him for a perfect opportunity, request him to grab his smartphone to make a call or browser something on the web and perform sleight of hand trick to install the app.
Keylogger for desktop users:
Keylogging applications for desktops are also installed in the same manner as the cellphones and work exactly the same.